Phreaky Writeup - Cyber Apocalypse 2024
→ 1 Introduction
This writeup covers the Phreaky Forensics challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘medium’ difficulty. The challenge involved the forensic analysis of a PDF emailed in multiple, password protected parts.
The description of the challenge is shown below.
→ 2 Key Techniques
The key techniques employed in this writeup are:
- Extracting SMTP emails from a packet capture
- Writing a shell script to automate decoding of the emailed attachments
- Reassembling the attachments into a single file
→ 3 Artifacts Summary
The downloaded artifact had the following hash:
$ shasum -a256 forensics_phreaky.zip
973180a558e14a6ff779765bb34b0e8fb59019d80836a9f548b583237bc3c3a2 forensics_phreaky.zipThe zip file contained a single packet capture file:
$ unzip forensics_phreaky.zip
Archive: forensics_phreaky.zip
inflating: phreaky.pcap
$ shasum -a256 phreaky.pcap
f29f0ad6482a1920c72314044b40fb916d2e5db6f1428cc835c12c36457c7c50 phreaky.pcap→ 4 Packet analysis
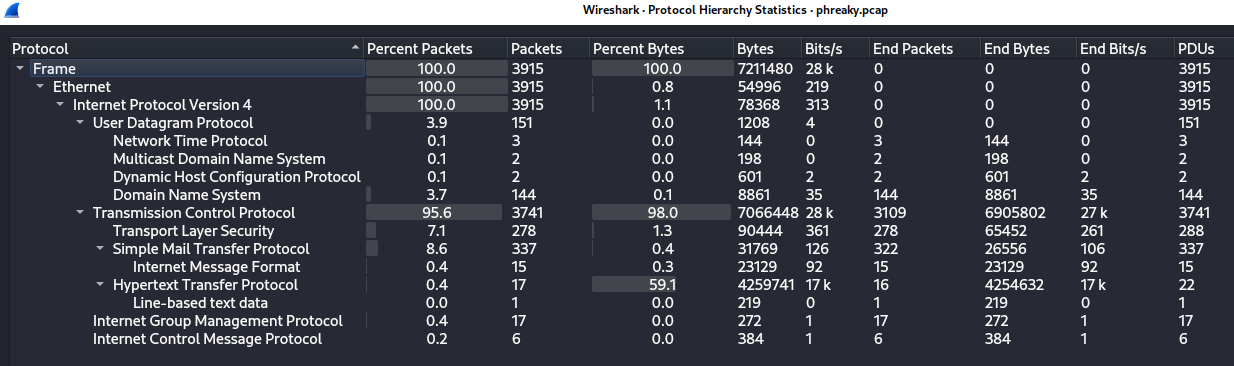
phreaky.pcap was opened in Wireshark. The
Statistics->Protocol Hierarchy menu indicated there were
two main protocols in use:
- HTTP
- SMTP
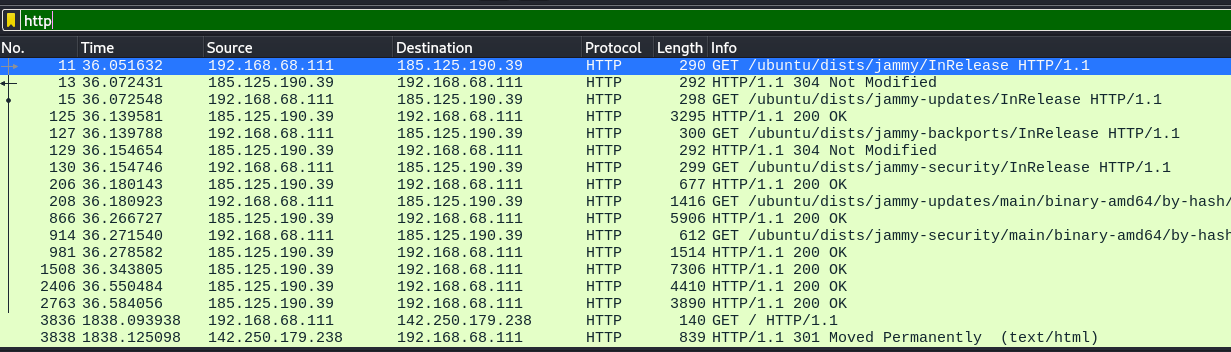
→ 4.1 HTTP traffic identified as benign
The HTTP traffic was identified as benign Ubuntu update requests and therefore irrelevant to the challenge:
→ 4.2 SMTP traffic identified as suspicious
The SMTP traffic involving 192.168.68.108 was identified as suspicious, with multiple emails being sent with a zip attachment and what appears to be a password for the attachment. The Wireshark “Follow TCP Stream” feature was used to easily view the communication for a given TCP stream.
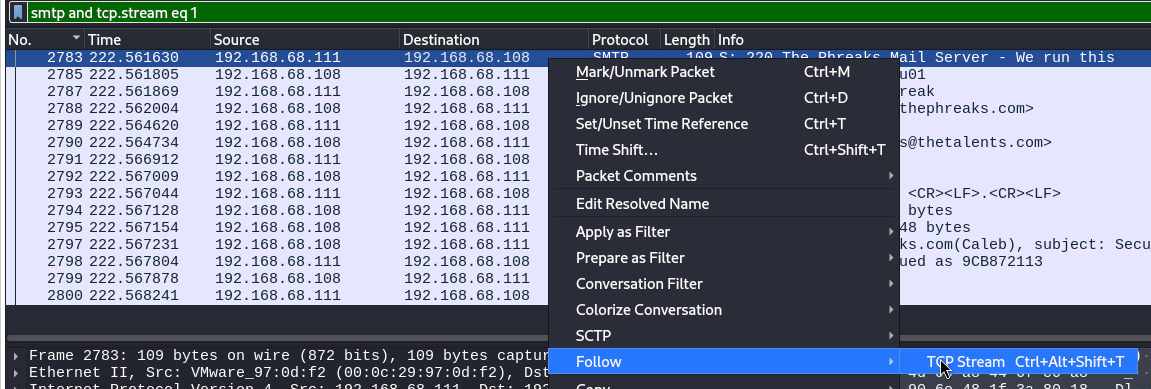
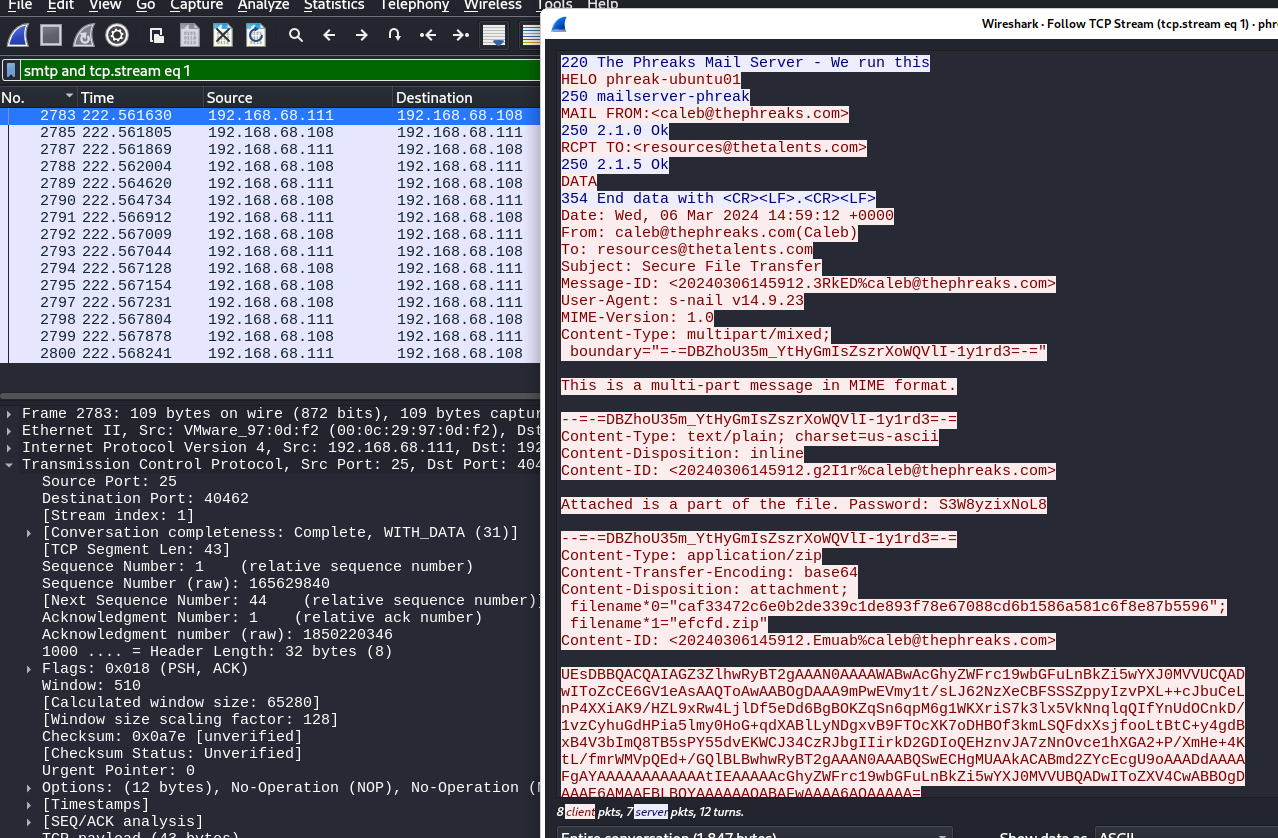
→ 5 Extracting the suspicious SMTP streams
Each suspicious, plaintext SMTP TCP stream was followed in Wireshark as above1 and saved to a file named with the stream number, resulting in the following files:
smtp-tcp-stream-01.txt
smtp-tcp-stream-03.txt
smtp-tcp-stream-05.txt
smtp-tcp-stream-07.txt
smtp-tcp-stream-09.txt
smtp-tcp-stream-11.txt
smtp-tcp-stream-13.txt
smtp-tcp-stream-15.txt
smtp-tcp-stream-17.txt
smtp-tcp-stream-19.txt
smtp-tcp-stream-21.txt
smtp-tcp-stream-23.txt
smtp-tcp-stream-25.txt
smtp-tcp-stream-27.txt
smtp-tcp-stream-30.txt→ 6 Extracting the zip files from each TCP stream
An extract-all.sh bash script was written to unzip the
files contained by the TCP streams.
#!/bin/bash
for stream in smtp-tcp-stream*.txt ; do
password=$(sed -Ene '/^Content-ID/,/^--=/p' "$stream"|grep -Po 'Password: (.*)'|sed -Ee 's/Password: //')
zip_filename=$(grep -Po 'filename.*\.zip' "$stream"|sed -Ee 's/.*"//')
base64_file_data=$(sed -Ene '/^Content-ID/,/^--=/p' "$stream"|grep -Pv -e 'Content|--|Attached'|grep -P '\w+')
echo "processing $stream"
echo "password:$password"
echo "zip_filename:$zip_filename"
echo -n "$base64_file_data" | base64 -d > "$zip_filename"
unzip -P "$password" "$zip_filename"
doneThe noteworthy features of the script are:
-
Line 3 is a for loop that loops through every stream file
-
Line 4 extracts the password from the stream using
sedandgrepin multiple steps:-
Printing all lines between the regex
^Content-ID/and^--=sed -Ene '/^Content-ID/,/^--=/p' "$stream" -
Grepping for the regex
Password: (.*)'and only outputting the matched text (-o)grep -Po 'Password: (.*)' -
Stripping ‘Password:’ from the result using
sedsed -Ee 's/Password: //
-
-
Line 5 extracts the zip file name from the stream using
sedandgrepin multiple steps-
Grepping the stream for the regex
filename.*\.zipand only outputting the matched text (-o)grep -Po 'filename.*\.zip' "$stream" -
Stripping everything up until the last double quote character using
sedsed -Ee 's/.*"//'
-
-
Line 6 extracts the base64 encoded zip file from the stream using
sedandgrepin multiple steps:-
Same as Line 4, printing all lines between the regex
^Content-ID/and^--=sed -Ene '/^Content-ID/,/^--=/p' "$stream" -
Stripping out any lines matching the regex
Content|--|Attachedusing an inverse grep matchgrep -Pv -e 'Content|--|Attached' -
Grepping for one or more word characters
grep -P '\w+'
-
-
Line 11 base64 decodes the zip file
-
Line 12 unzips the zip file using the password obtained from line 4
The script was run, resulting in phreaks_plan.pdf.part*
files being extracted.
$ ./extract-all.sh
processing smtp-tcp-stream-01.txt
password:S3W8yzixNoL8
zip_filename:efcfd.zip
Archive: efcfd.zip
inflating: phreaks_plan.pdf.part1
processing smtp-tcp-stream-03.txt
password:r5Q6YQEcGWEF
zip_filename:17dbf.zip
Archive: 17dbf.zip
extracting: phreaks_plan.pdf.part2
<snip/>In total, the resulting files were:
$ ls -1 phreaks_plan.pdf*
phreaks_plan.pdf
phreaks_plan.pdf.part1
phreaks_plan.pdf.part10
phreaks_plan.pdf.part11
phreaks_plan.pdf.part12
phreaks_plan.pdf.part13
phreaks_plan.pdf.part14
phreaks_plan.pdf.part15
phreaks_plan.pdf.part2
phreaks_plan.pdf.part3
phreaks_plan.pdf.part4
phreaks_plan.pdf.part5
phreaks_plan.pdf.part6
phreaks_plan.pdf.part7
phreaks_plan.pdf.part8
phreaks_plan.pdf.part9→ 7 Reassembling the PDF file
The PDF file was reassembled using cat:
$ cat $(ls -1 phreaks_plan.pdf.part?) $(ls -1 phreaks_plan.pdf.part1?) > phreaks_plan.pdf
A minor trick was used to ensure the files were assembled in the
correct order. The following command substitution used a single
? wildcard at the end of the file name to match only parts
1 to 9:
$(ls -1 phreaks_plan.pdf.part?)
The following command substitution used a 1? at the end
of the file name to match only parts 10 to 15.
$(ls -1 phreaks_plan.pdf.part1?)→ 8 Obtaining the flag from the PDF
phreaks_plan.pdf was opened and the plaintext flag found
within:
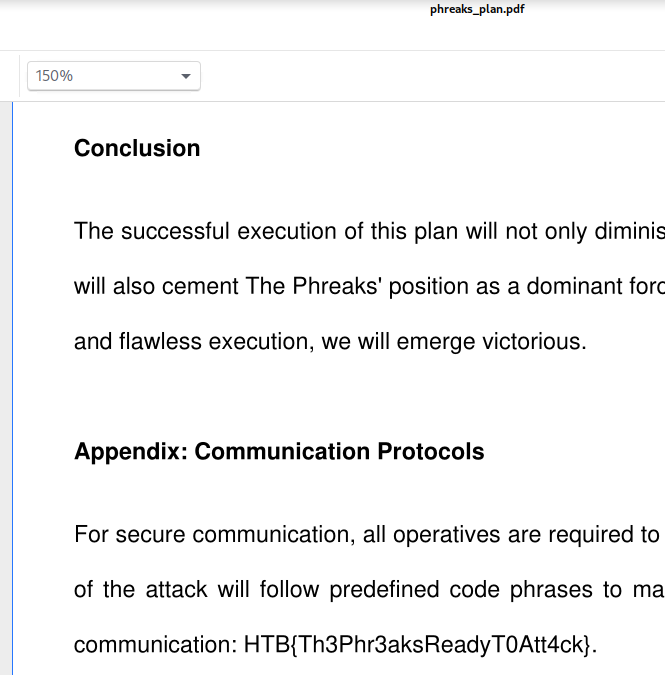
→ 9 Conclusion
The flag was submitted and the challenge was marked as pwned