PackedAway Writeup - Cyber Apocalypse 2024
→ 1 Introduction
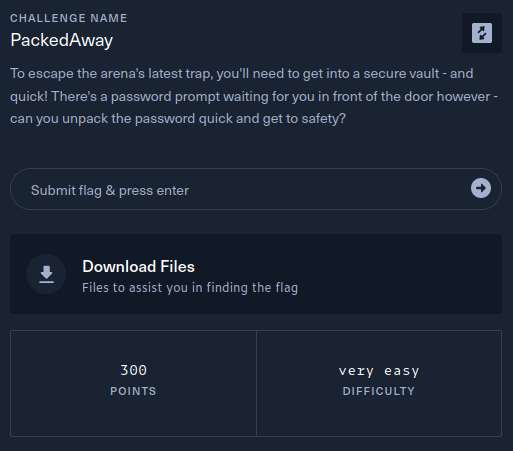
This writeup covers the PackedAway Reversing challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘very easy’ difficulty. The challenge involved unpacking a binary that has been UPX packed.
The description of the challenge is shown below.
→ 2 Key Techniques
The key techniques employed in this writeup are:
- Identifying a binary as being packed by UPX.
- Unpacking a UPX packed binary.
-
Using the
stringscommand to search for strings in a binary.
→ 3 Artifacts Summary
The downloaded artifact had the following hash:
$ shasum -a256 rev_packedaway.zip
090e1633afda48d2084373409a0988016127062488065a3e95148d9d953a0d49 rev_packedaway.zip
The zip file contained a single file, packed:
$ unzip rev_packedaway.zip
Archive: rev_packedaway.zip
creating: rev_packedaway/
inflating: rev_packedaway/packed
$ shasum -a256 packed
f246f7f5a246db91904a714b1d144f59685c3b27f538d0e6ac78a4c1022aef46 packed→ 4 Static Analysis
→ 4.1 Basic file identification
The file command was used to identify the binary. For
the purposes of the challenge, the key properties identified were:
- ELF: The binary is in ELF format, commonly used on Linux systems.
- x86-64: The binary is compiled for x86-64 bit machines.
$ file packed
packed: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), statically linked, no section header→ 4.2 Identification as UPX packed
Extracting strings from the binary using the strings
command, then using grep to filter the results for “upx”,
revealed the binary was packed with UPX:
$ strings packed|grep -i upx
UPX!
$Info: This file is packed with the UPX executable packer http://upx.sf.net $
$Id: UPX 4.22 Copyright (C) 1996-2024 the UPX Team. All Rights Reserved. $
UPX!u
UPX!
UPX!→ 4.3 UPX unpacking
The binary was unpacked using the upx command:
$ upx -d packed
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2024
UPX 4.2.2 Markus Oberhumer, Laszlo Molnar & John Reiser Jan 3rd 2024
File size Ratio Format Name
-------------------- ------ ----------- -----------
22867 <- 8848 38.69% linux/amd64 packed
Unpacked 1 file.→ 4.4 Basic file identification after unpacking
The unpacked file is also an ELF x86-64 binary:
$ file packed
packed: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=d24a6e8eef367eb565e8bb90fe3ef9e9d0a71a43, for GNU/Linux 3.2.0, not stripped→ 4.5 Obtaining the flag
The flag was trivially found by extracting strings from the unpacked
binary using the strings1 command, then using
grep to filter the results for “HTB”, with the last string
found being the flag.
$ strings packed|grep HTB
HTB{unp4ck3dr3t_HH0f_th3_pH0f_th3_pH0f_th3_pH0f_th3_pH
HTB{
HTB{unp4ck3d_th3_s3cr3t_0f_th3_p455w0rd}→ 5 Conclusion
The flag was submitted and the challenge was marked as pwned