Makeshift Writeup - Cyber Apocalypse 2024
→ 1 Introduction
This writeup covers the Makeshift Crypto challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘very easy’ difficulty. The challenge involved implementing a decoder for a provided Python encoder.
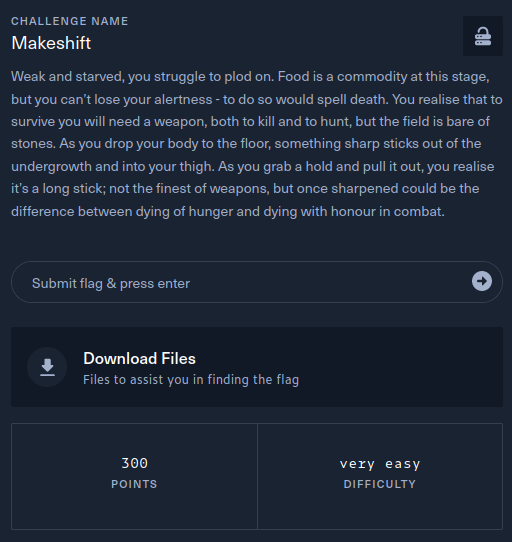
The description of the challenge is shown below.
→ 2 Key Techniques
The key techniques employed in this writeup are:
- Manual Python source code review
- Adapting existing Python source code
→ 3 Artifacts Summary
The downloaded artifact had the following hash:
$ shasum -a256 crypto_makeshift.zip
a692a0c129fe0bb43190d6133d2e5ec52beb7e5261bf5fd541028e761047304d crypto_makeshift.zip
The zip file contained a single Python source code file,
source.py, and output.txt:
$ unzip crypto_makeshift.zip
Archive: crypto_makeshift.zip
creating: challenge/
inflating: challenge/source.py
extracting: challenge/output.txt
$ shasum -a256 challenge/*
f54f516a925e53b3cf97cb4b21c01c9bb36821582d18ac06d07f9ec5fed9d589 challenge/output.txt
b5c59a96f342d04b4d782a418c907c3d77039c9b24022f75fc11ec7aad24444c challenge/source.py
→ 4 Static Analysis
→ 4.1 output.txt
output.txt was presumed to contain the encoded flag,
given the presence of ‘THB’ at the end:
$ cat output.txt
!?}De!e3d_5n_nipaOw_3eTR3bt4{_THB→ 4.2 source.py
source.py contains Python code that encodes the flag as
follows:
- Line 3 reverses the flag
- Lines 6-9 swaps characters within every 3 character block by cyclically rotating characters left. For example ‘123’ becomes ‘231’
from secret import FLAG
flag = FLAG[::-1]
new_flag = ''
for i in range(0, len(flag), 3):
new_flag += flag[i+1]
new_flag += flag[i+2]
new_flag += flag[i]
print(new_flag)→ 5 Implementing the decoder
decode.py was implemented that does the opposite of what
source.py does:
-
Lines 1-2 read the encoded flag from
output.txt -
Lines 6-10 reverse the 3 character block encoding performed by
source.py - Line 12 prints the reversed flag
with open("output.txt", "r") as f:
flag = f.read().strip('\n')
new_flag = ''
for i in range(0, len(flag), 3):
# encrypted as middle, last, first so we decrypt back
new_flag += flag[i+2]
new_flag += flag[i]
new_flag += flag[i+1]
print(new_flag[::-1])→ 6 Obtaining the flag
The script was run and the flag was obtained:
$ python3 decrypt_writeup.py
HTB{4_b3tTeR_w3apOn_i5_n3edeD!?!}→ 7 Conclusion
The flag was submitted and the challenge was marked as pwned