Flag Command Writeup - Cyber Apocalypse 2024
→ 1 Introduction
This writeup covers the Flag Command Web challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘very easy’ difficulty. The challenge was a black box web application challenge.
The description of the challenge is shown below.
→ 2 Key techniques
The key techniques employed in this writeup are:
- analyzing basic HTTP responses
- manual client side JavaScript source code review
→ 3 Mapping the application
→ 3.1 Mapping the application interactively
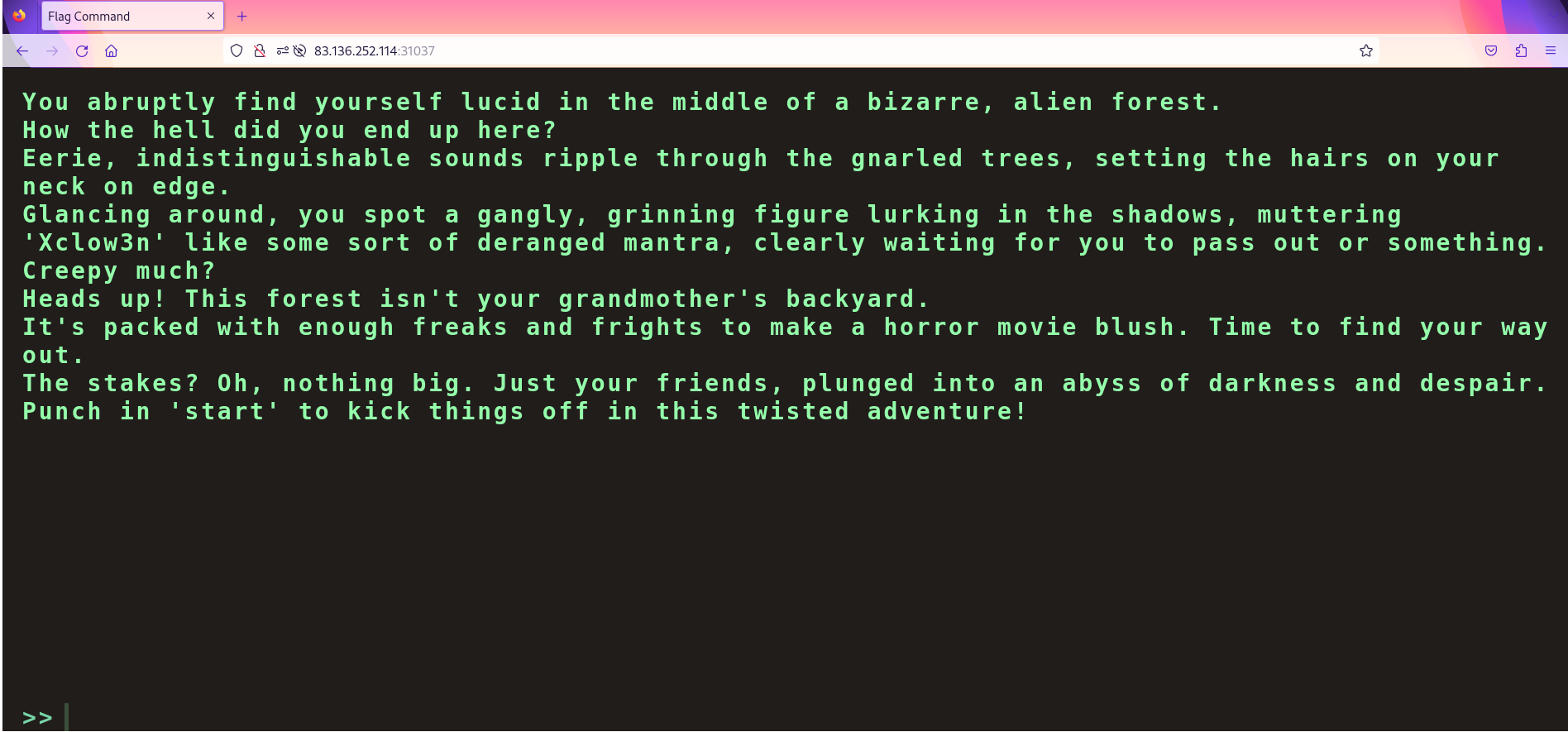
The target website was opened in the Firefox browser, proxied via mitmproxy. The website displayed a terminal-like prompt.
→ 3.2 Mapping the application via client side source code review
In mitmproxy, a couple of key responses were
observed:
-
GET
/api/optionsreturned a JSON response containing a ‘secret’ option: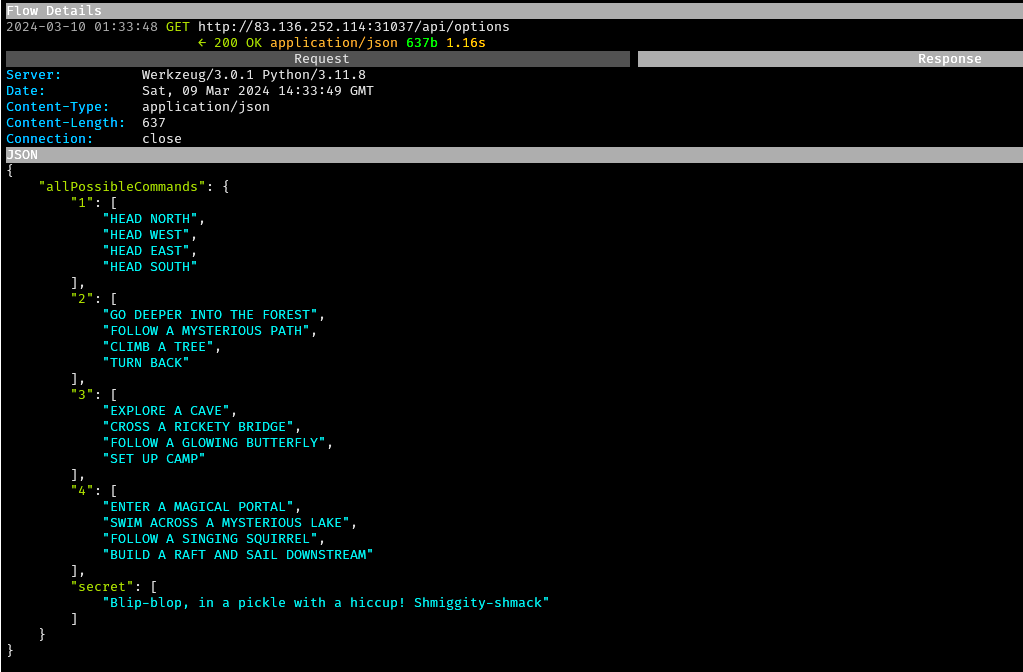
-
The JavaScript code in
/static/js/terminal/main.jstests whether the current step in the options contains thecurrentCommandor thecurrentCommandequals the secret option. If it does, it POSTs thecurrentCommandto the/api/monitorendpoint as JSON{"command":currentCommand}.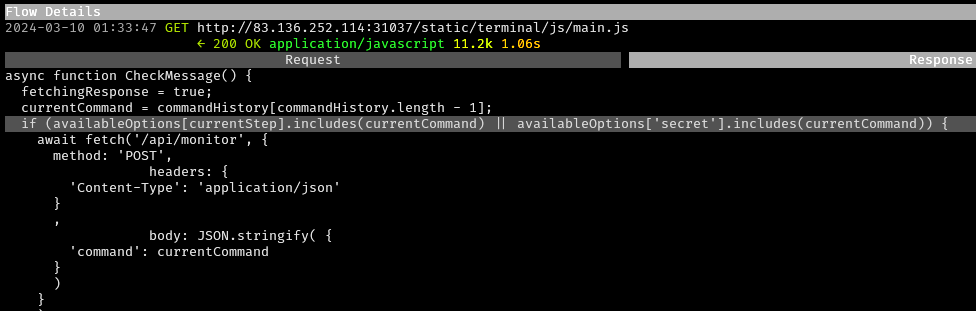
→ 4 Obtaining the flag
-
The secret option was POSTed to the
/api/monitorendpoint: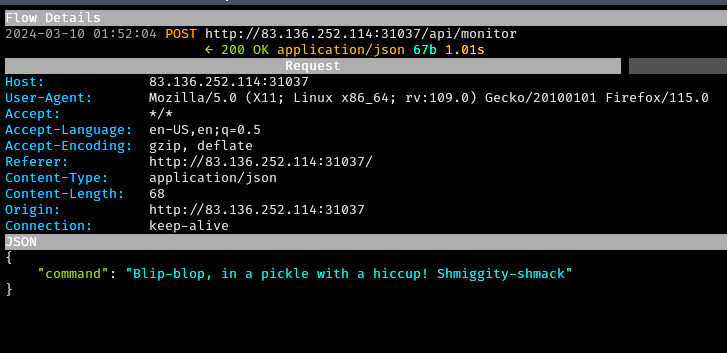
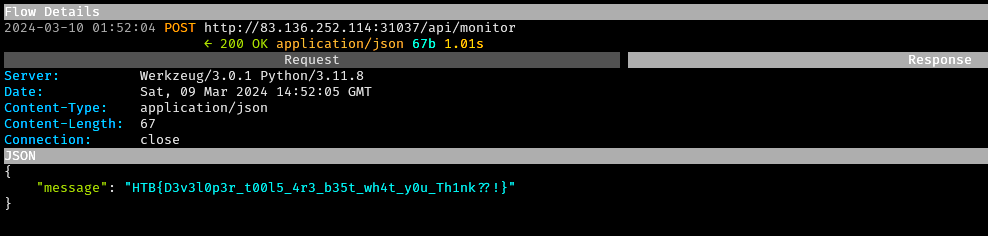
-
The response contained the flag:
→ 5 Conclusion
The flag was submitted and the challenge was marked as pwned