BunnyPass Writeup - Cyber Apocalypse 2024
→ 1 Introduction
This writeup covers the BunnyPass Hardware challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘very easy’ difficulty. The challenge involved gaining access to a RabbitMQ Management UI using default credentials.
The description of the challenge is shown below.
→ 2 Key Techniques
The key techniques employed in this writeup are:
- Researching default credentials for the RabbitMQ Management UI
- Manual enumeration of a web application
→ 3 Mapping the application interactively
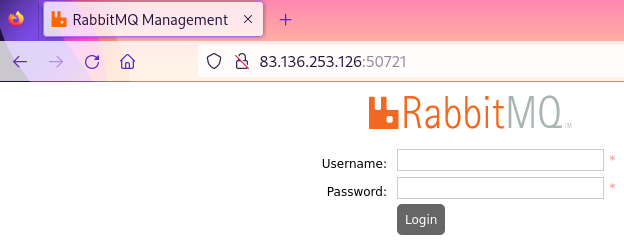
The target website was opened in the Firefox browser, proxied via mitmproxy. The website displayed a login form for the RabbitMQ Management UI.
→ 4 Vulnerability analysis - default credentials
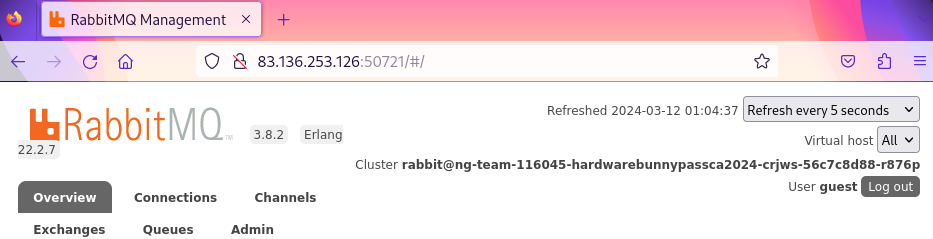
From the challenge description, default credentials will provide
access to the site. The product
documentation indicated that default credentials of
guest:guest should work for the management UI. These
successfully granted access. This is an instance of common weakness CWE-1392: Use of
Default Credentials.
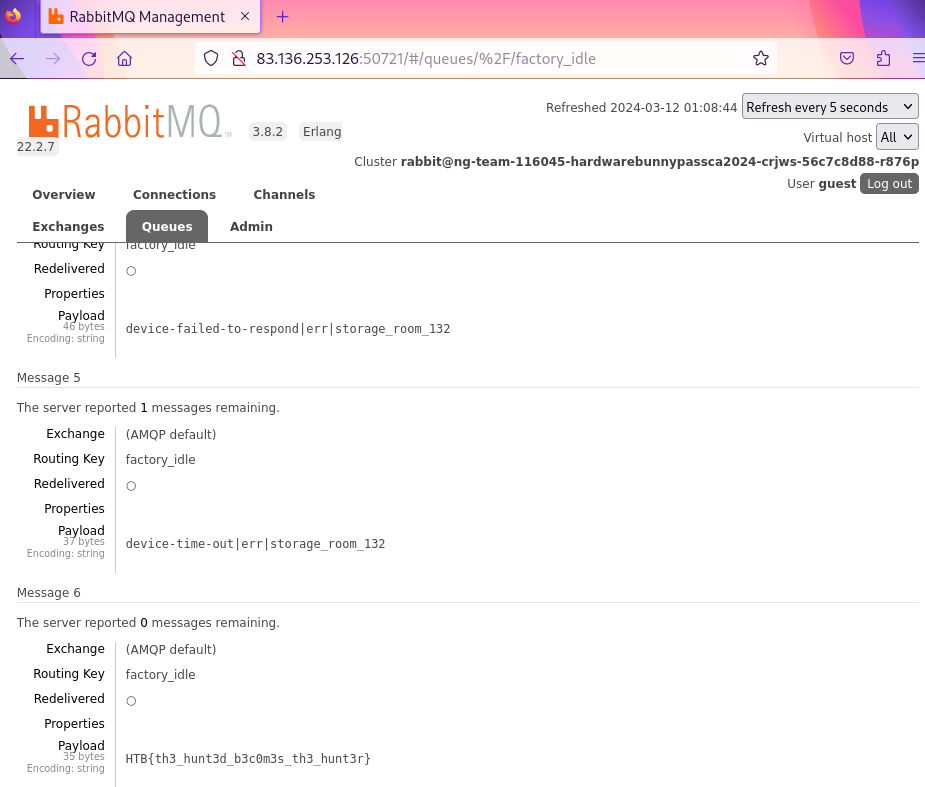
→ 5 Obtaining the flag
The UI was manually enumerated. The flag was found in the last
message on the factory_idle message queue.
→ 6 Conclusion
The flag was submitted and the challenge was marked as pwned